Get in Touch
Our team is happy to answer your questions. Fill out the form and we’ll get back to you as soon as possible.
Threat Detection Model Enhanced by Artificial Intelligence and Machine Learning Techniques for Hackless
Time-to-Market
3 months
Blockchain
Ethereum
Project Stage
Prototype
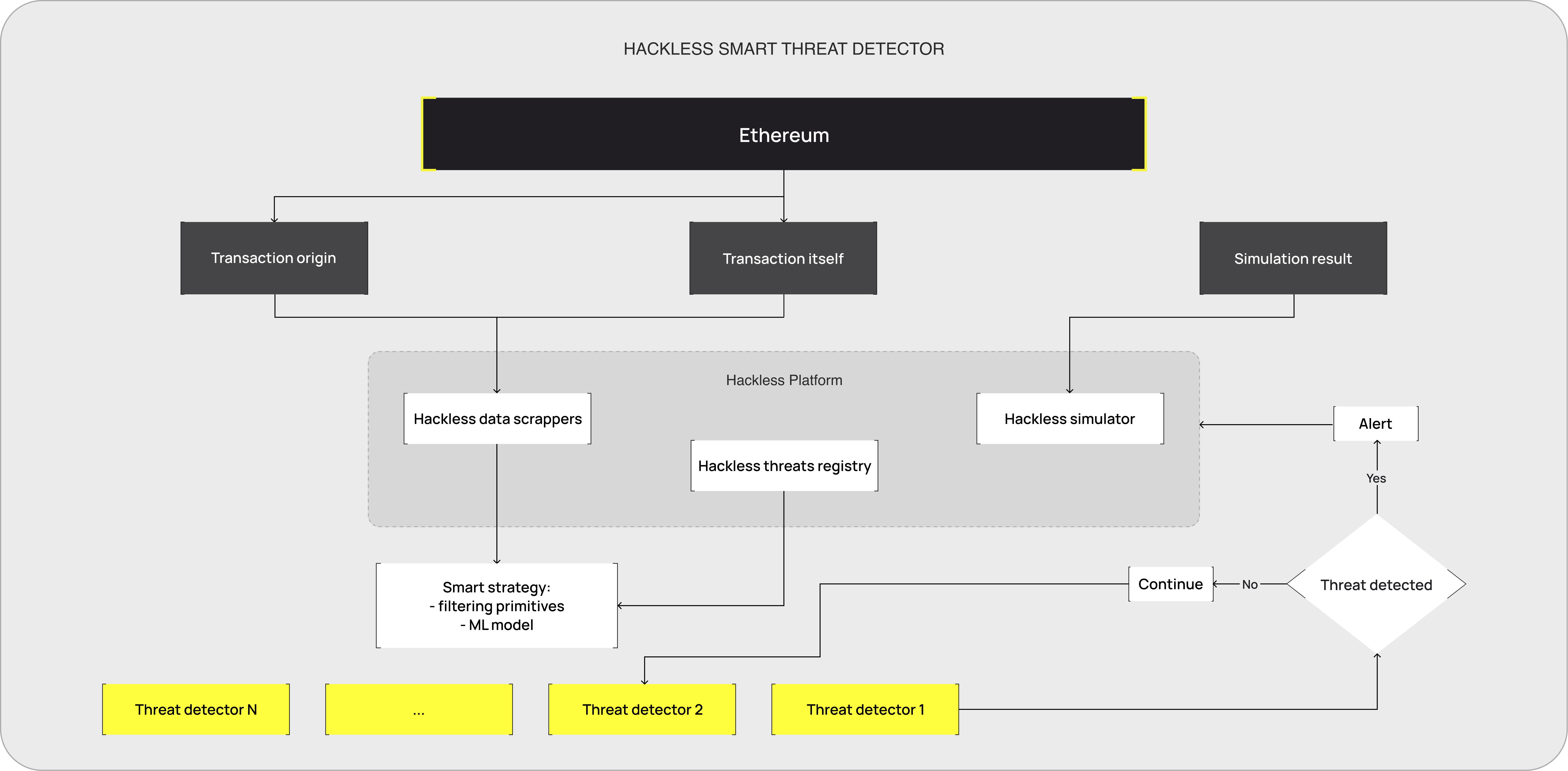
Hackless, a project focusing on web3 security, aims to address two critical areas of protocol life cycles: early detection of suspicious transactions and rescue of funds from compromised protocols. Blaize specialists from Intelligence and Security teams managed to design and implement a smart, AI/ML-enhanced threat detection system for Hackless.
Hackless aimed to leverage AI/ML enhancements for early detection of suspicious transactions and rescue operations in the event of protocol hacks. The task set for the Blaize team was to create a prototype for this model, an abstract and non-trivial job that required a great deal of brainstorming, planning, and collaboration with the Hackless team.
The project was devided into several stages, beginning with the identification of input parameters for the model. Blaize had to collate transaction origins, transaction details, and simulation results. This set of parameters enabled them to build a reliable, predictive model.
After setting the parameters, the team went through the standard pipeline for the sake of creating the most productive model and did it successfully.
The Blaize Security team worked with the Intelligence team, validating the threats the model needed to detect and providing necessary corrections. The Security team also contributed to model output validation and the feedback loop for model re-training.
Learn more
The team comprised various specialists, including Data Engineers, ML specialists, DevOps engineers and our Security team. We used several tools and languages for this project, including Python and R. The team relied on ML: decision trees, regression models, supervised classification, and Naive Bayes filtering. The development process was organized in a systematic way, with major milestones:
1
Q1 2023
Brainstorming on the project pipeline, researching necessary inputs (from transactions in the mempool) and outputs (threats and attacks to be detected). Choosing input parameters and building a feedback loop from the output.
2
Q1 2023 - Q2 2023
Scrapping necessary data and building the dataset. Constructing and training several models. Development of the system of filtering primitives for trivial threats detection based on input parameters.
3
Q2 2023
Experiments stage to choose the best-performing model. Models tuning based on their outputs validation by the Security team. Final prototype testing on the recent data.
Our team is happy to answer your questions. Fill out the form and we’ll get back to you as soon as possible.
Our team can offer a consultation to discuss all your ideas and help your business take the next step