SECURITY AUDIT FOR PROMETHIUM

At Blaize, we take pride in securing the decentralized ecosystem, and our latest milestone was to conduct a comprehensive security audit for Promethium protocol. With a commitment to ensuring the safety and trustworthiness of DeFi projects, we meticulously examined both the smart contracts of Promethium and the backend rebalancer worker to identify vulnerabilities and provide actionable recommendations.
ABOUT THE PROJECT
Promethium is an automated lending and borrowing optimizer protocol. And it doesn’t stop there. Promethium also comes with a toolkit for managing deposits, loans, and liquidity-mining rewards.
During the audit, we examined the security of smart contracts and the backend service for the Promethium protocol. Our task was to find and describe any security issues in the smart contracts of the platform and explore the backend service which actually performs funds rebalancing between the protocols. Thus, this platform security audit was performed in 2 iterations and this report presents the findings from both. Also, auditors performed additional reviews of the deployed code (to check correct settings and roles distributions) and code upgrades – these notes are also included into the report.
Promethium contracts represent a module of rebalancing positions in various external DeFi protocols with the main contract of Vault type, inheriting the ERC-4626 standard. The audit’s objective was to ensure that these contracts functioned correctly and maintained a known security level.
During the second audit iteration, our team has been working on auditing Promethium backend components. The Rebalancer service is a sophisticated instrument that provides the active operating part of the protocol. It calculates APR of the integrated protocols, chooses the best one to re-deposit funds, and handles rebalance activities in a protocol. Thus, it interacts with smart contracts, manages the rebalance strategies, and withdrawals queue.
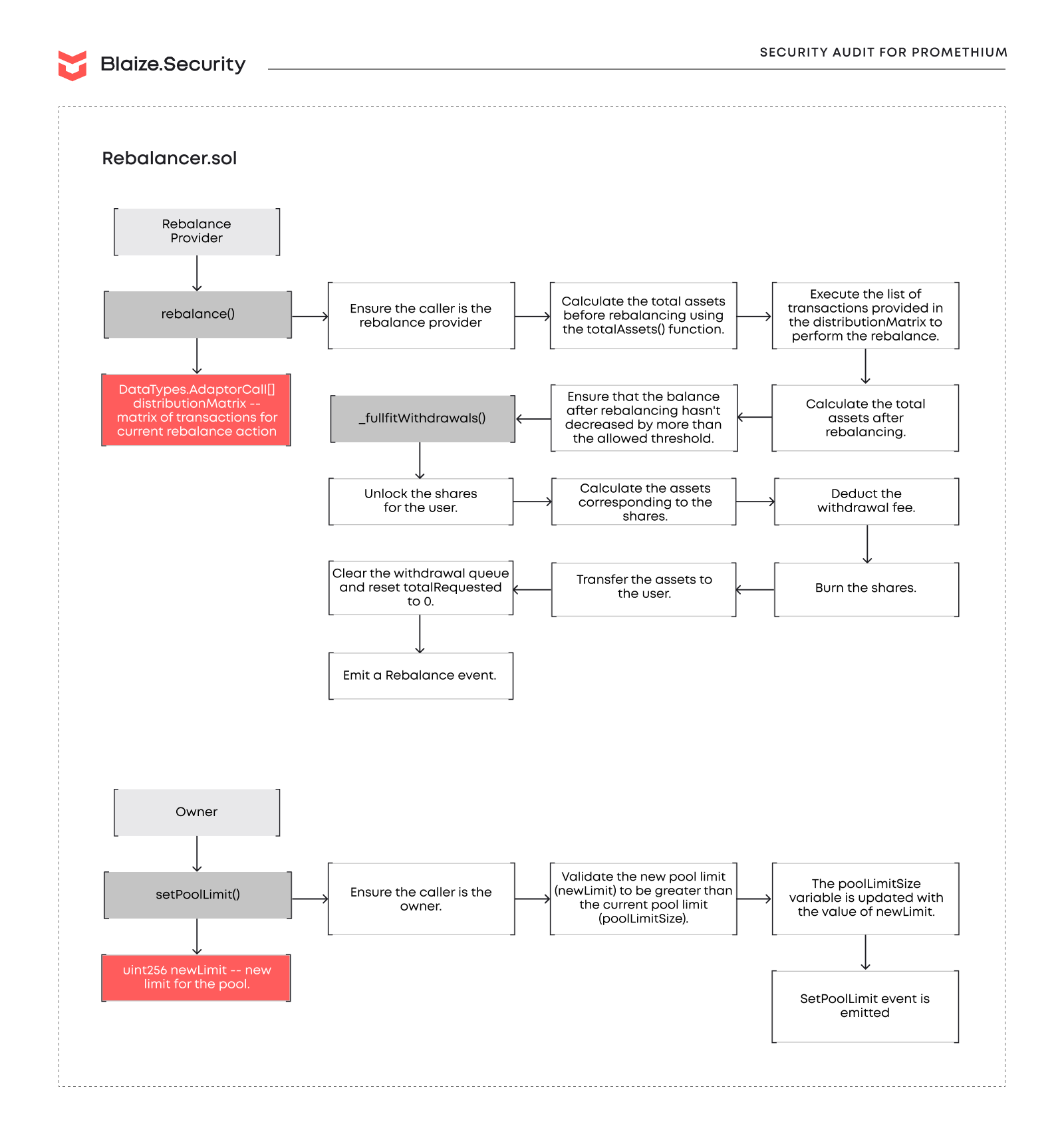
MAIN REQUIREMENTS
During our audit, we scrutinized the smart contracts and the backend service for various vulnerabilities in several stages:
1) Standard smart contracts vulnerabilities checklists, including but not limited to:
- Reentrancy
- Gas limit and loops
- Transaction-ordering dependence
- Slippage tolerance
- Denial-of-Service (DoS) attacks
- Resistance against flash loans and frontrunning
- Storage issues (uninitialized, unused, etc) and incorrect local variable usage
- Upgradeability issues
and other potential Solidity vulnerabilities and attack vectors;
2) Business logic decompositions to find loopholes, deadlocks, hidden backdoors, incorrect math and calculations, malicious code injections, and other flow-related issues;
3) Review of the access control tree and roles distributions for smart contracts and correct integration of mulstisig components into the backend service
4) Review of dependencies, integrations, and 3rd parties, verified with appropriate integration tests;
5) Structure of the backend, the architecture of the sub-services, correctness of keys storage and usage;
6) Correctness of the APR calculations, the rebalance strategy, interaction between the backend and smart contracts, rebalancing routines;
7) Our own internal security checklists, additionally verified during the testing stage. The team had the main focus on verifying the correctness of implemented liquid staking mechanics.
SMART CONTRACT SECURITY AUDIT PROCEDURE
Our audit process encompassed manual and testing stages (for both audit iterations):
1.MANUAL AUDIT STAGE
- Manual line-by-line code review by 2 security auditors with crosschecks and validation from the security lead;
- Vulnerabilities analysis against several checklists, including internal Blaize.Security checklist;
- Business logic inspection;
- Protocol decomposition and components analysis with building interaction schemes and sequence diagrams;
- Storage usage review and gas optimization review – keys storage and usage for the backend service;
- Math operations and calculations analysis – that included APR calculations for the backend service;
- Access control and roles structure review – including multisig handling by the backend;
- Review of dependencies, 3rd parties, and integrations;
- Review with automated tools and static analysis;
- Code quality, documentation, and consistency review.
2.TESTING STAGE
- Development of edge cases based on manual stage results;
- False positives validation;
- Integration tests for checking connections with 3rd parties;
- Manual exploratory tests over the locally deployed protocol;
- Checking the existing set of tests and performing additional unit testing;
- End-to-end test for the backend service
Upon completion of the audit, we delivered a comprehensive smart contract security analysis report to the Promethium team. This report included:
- Identified risks
- Potential mitigations
- Detailed vulnerability assessments
- Recommendations for improvements
A COMPLEX AUDIT IS AN EXCELLENT OPPORTUNITY TO ENHANCE THE LEVEL OF SECURITY FOR YOUR PROJECT. LEARN MORE ON BLAIZE WEBSITE.
AUDIT RESULT
The Blaize Security team successfully conducted an audit of the Promethium protocol, an automated lending and borrowing optimizer protocol on Arbitrum. Our meticulous audit process involved an examination of every line of code, with our experienced auditors cross-referencing each element against comprehensive vulnerabilities checklists and covering all components with a customly developed auditing strategy. The outcome of this analysis revealed a commendable level of security in both the smart contracts and the backend services that constitute the Promethium protocol.
While the smart contracts and the backend service overall security were robust, several medium-severity issues and low-severity issues were identified during the audit. The Promethium team has resolved them and demonstrated their commitment to the continuous improvement of their platform and the safety of user assets.
In conclusion, the Promethium protocol demonstrated a high level of security, which was estimated by Blaize as Highly Secure at 9.75 out of 10. Throughout our examination of the project, the auditing team verified the chosen protocol architecture and its business solutions regarding the access control and model of interaction between the components. The codebase is organized, making it easier to navigate and understand. It follows best practices, demonstrating a balance between functionality and clarity. The team has shown a solid strategy for the mitigation of risks of keys’ storage vulnerabilities and future logic optimization.
Take a closer look at Promethium security report on Blaize.Security Github.




