SMART CONTRACT SECURITY AUDIT FOR AURORA

Aurora is an EVM on the NEAR Protocol blockchain that delivers a turn-key solution for developers to operate their apps on an Ethereum-compatible platform. It was presented in May 2018 as the answer to the challenges related to scaling, speed, and security faced by this blockchain generation.
Aurora is currently the most advanced solution on the market and will probably remain such for a significant time. With Aurora, Ethereum users can work with familiar applications while benefiting from the efficiency of NEAR, removing significant financial barriers for users and developers.
ABOUT THE PROJECT
The Blaize team has conducted the security audit for the Aurora set of smart contracts, including Treasury.sol, AdminControlled.sol, and JetStakingV1.sol. You can see how these smart contracts work on the graph below.
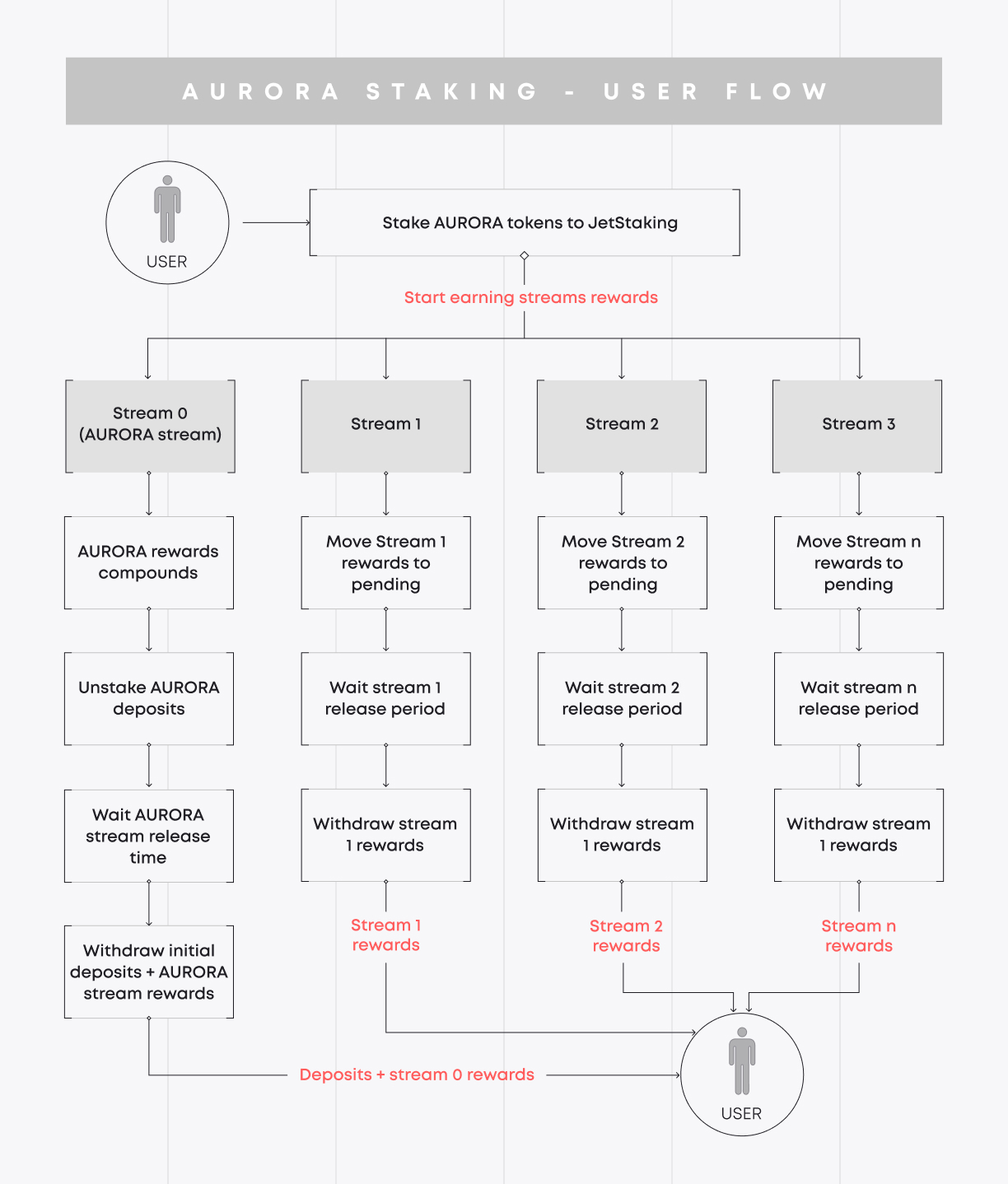
As you can see, users can stake their AURORA tokens and earn multiple rewards. These rewards are divided into streams, each with its own reward token.
Users, who have staked AURORA, start to earn rewards from these streams and can claim pending rewards at any time. However, they need to wait before withdrawing rewards to their wallets.
Users can withdraw rewards in AURORA tokens from a special stream when they unstake their deposited tokens.
MAIN REQUIREMENTS
We were assigned to detect and describe security issues in the Aurora EVM smart contract set.
We needed to check the smart contracts with the following parameters:
- Whether the contract is secure;
- Whether the contract corresponds to the documentation;
- Whether the contract meets best practices regarding the efficient use of gas and code readability.
During the audit, we checked the code against the standard set of vulnerabilities like reentrancy, gas limits, loops, unsafe external calls, correct storage initialization and usage, timestamp dependencies, etc.
Furthermore, the auditors’ team fully investigates the smart contracts’ business logic and security checks against the loopholes and vulnerabilities from the Blaize.Security knowledge base:
- Access control checks: correct roles assignment, privilege roles abilities, correct identification of public functions for regular users;
- Funds flow: correspondence of withdrawing to deposit, correct approves and token transfers logic, double spending absence, correct operations with different assets and correct conversion between the assets, no funds blocked and locked forever;
- Math and calculations: dust attacks, correct math operations, extra-tokens attacks, muldiv patterns, and correct accuracy;
- Correct initialization parameters;
- Correct fungible tokens usage, absence of fake tokens attacks, and safe ERC20 usage.
- Time dependency, the correct sequence of method calls, absence of deadlocks.
SECURITY AUDIT PROCEDURE FOR AURORA SMART CONTRACT
Blaize.Security has an established security audit procedure. It includes the following steps:
- Check for code consistency and whether the contract corresponds to the documentation;
- Checks against the standard list of vulnerabilities we have mentioned above;
- Static analysis by automated tools;
- Manual code analysis and code quality review;
- Business logic review and protocol scheme preparation
- Gas usage analysis;
- Unit tests coverage check;
- Creation of the custom set of unit tests for full coverage;
- Exploratory testing and additional scenarios for use-cases coverage;
- Security analysis report;
- Post-audit fixes review.
See another smart contract audit case here: Smart Contract Security Audit for Crypto Collective.
AUTOMATED TOOLS ANALYSIS
The team has checked the contract with the help of several publicly available automated analysis tools, such as Mythril, Solhint, Slither, and Smartdec. Also, we have done manual verification of all the issues detected by automated tools.
MANUAL CODE REVIEW
Manual testing is necessary to analyze all the previously found vulnerabilities and check the operational work of smart contracts in general. In addition, manual code review includes checking smart contract logic and comparing it with the one described in the documentation.
SECURITY ANALYSIS REPORT
In the end, we have provided a smart contract security analysis report for Aurora. The document contains all detected risks and the possible variants of its mitigations, issues, vulnerabilities details, and recommendations for their improvements.
NEED A SMART CONTRACT AUDIT TOO? CHECK ALL BLAIZE SECURITY SERVICES.
AUDIT RESULT
Aurora’s smart contracts have no critical security problems in line with the assessment. The code is high-quality, well-documented, and has good native test coverage. All unclear or suspicious functionality was verified with the Aurora team and fully covered with additional tests. Additionally, the Aurora team successfully resolved all found issues connected to the problems with funds flow and incorrect rewards schedules.
Thus, according to the above rules, we consider the overall Aurora smart contract security level as Highly Secure, 9.9 out of 10.
The audit document with the full list of identified vulnerabilities and recommendations for their improvements can be found below:
Aurora-smart-contract-audit_compressed



