SMART CONTRACT SECURITY AUDIT FOR SYNTHEX

SyntheX is a DeFi system that allows users to mint synthetic assets backed by collateral assets. The main functionality of SyntheX are:
- Reward Distribution: The distribution of rewards for liquidity providers in various pools.
- Collateral Management: Management of collateral assets, including depositing, withdrawing, enabling/disabling collateral, setting collateral caps, and volatility ratios.
- Trading Pools: The contracts enable/disable trading pools and manage volatility ratios.
- Access Control: The contracts include functions for managing access control, pausing/unpausing the contract, and updating addresses for various components.
ABOUT THE PROJECT
The audited protocol is a synthetics platform based on the overcollaterization principle. The platform receives collateral deposits from users and mints synthetics by the linear utilization rate together with debt tokens for the user. Therefore the platform also combines features from the lending protocol since it enables the liquidation process for accounts under the collateral requirement.
For user incentivization, the platform provides rewards distributions for liquidity providers and SYX token providers (via the esSYX contract). More info about the protocol (including admins functions) is described in the “Protocol Overview” section in the report attached to the case below.
The scheme below shows a part of SyntheX smart contract, Blaize.Security audited.
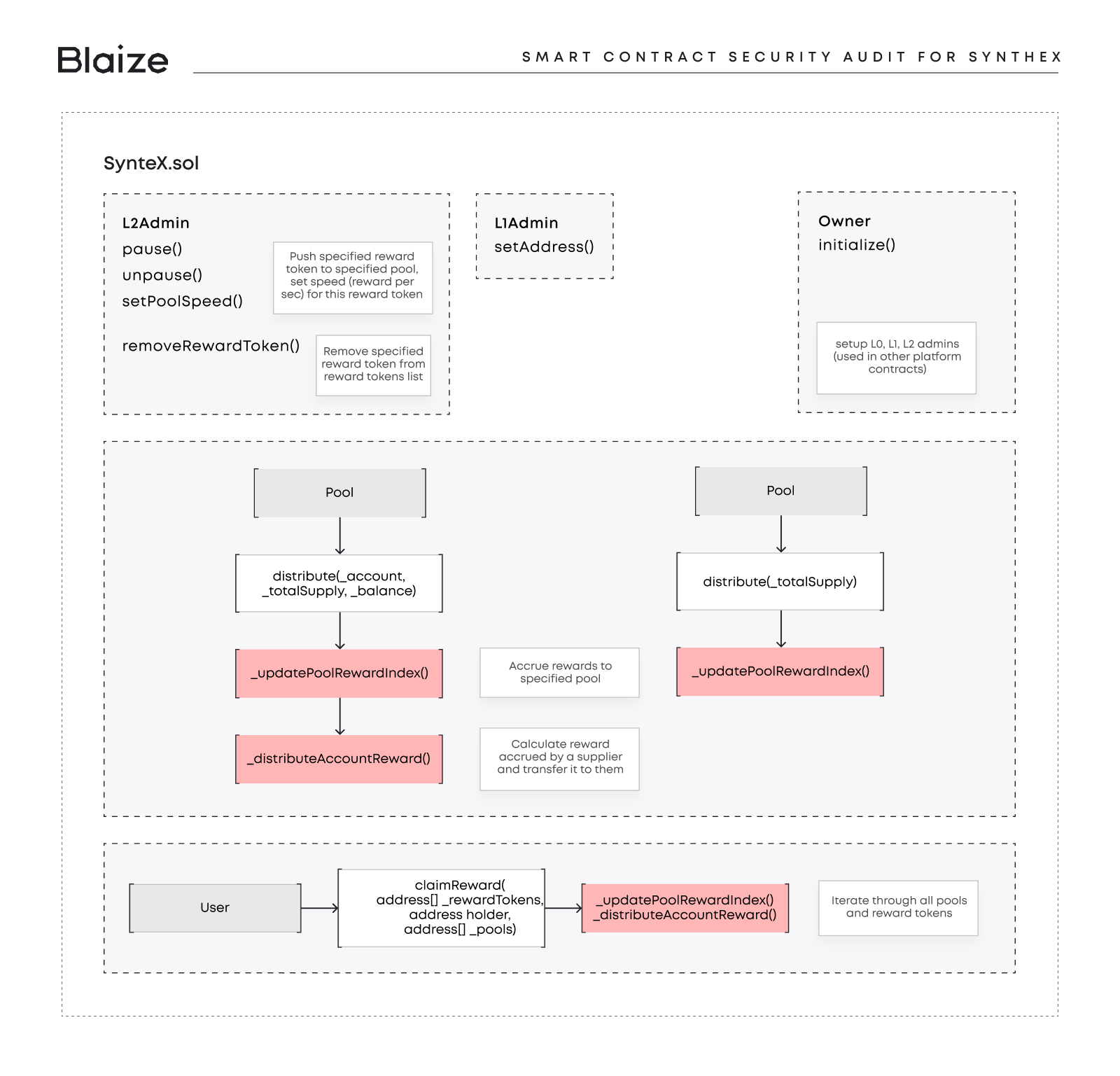
MAIN REQUIREMENTS
Blaize’s task was to find and describe security issues in the smart contracts of the platform.
We needed to check the SyntheX protocol with the following parameters:
- Whether contracts the collateral deposit is secure;
- Whether the rewards distribution works as expected;
- Whether the liquidation mechanics is correct;
- Whether the implemented functionality corresponds to the documentation;
- Whether contracts meet best practices in efficient use of gas and code readability.
We have scanned both sets of smart contracts for commonly known and more specific vulnerabilities:
- Unsafe types conversion and unsafe math;
- Timestamp Dependence;
- Reentrancy (for Solidity part);
- Correct roles distribution and access control flow;
- Gas Limit and Loops;
- Transaction-Ordering Dependence;
- DoS attacks with (Gas Limit, unexpected reverts, storage abuse, etc.);
- Byte array vulnerabilities;
- Style guide violation;
- ERC20 standard correspondence and correct tokens usage;
- Uninitialized state/storage/ local variables;
In addition, the SyntheX protocol was checked against less common vulnerabilities from the internal Blaize.Security knowledge base.
SMART CONTRACT SECURITY AUDIT PROCEDURE
Blaize.Security has an established security audit procedure. It includes the following steps:
- Manual code review;
- Static analysis by automated tools;
- Business logic review and decomposition of the system;
- Unit test coverage check;
- Extensive integration testing;
- Fuzzy and exploratory testing;
- Providing a detailed report of detected issues;
- Verification of fixes;
- Final audit report preparation & publishing.
Last time Blaize specialists successfully finished an audit for another DeFi big player – find more details here.
AUTOMATED TOOLS ANALYSIS
We scanned the contracts using several publicly available automated analysis tools such as Mythril, Solhint, Slither, and Smartdec. All issues found were verified manually.
MANUAL CODE REVIEW
We manually analyzed the smart contracts to identify potential security vulnerabilities. Our analysis involved a comparison of the smart contract logic with the description provided in the documentation.
UNIT TEST COVERAGE
The audit scope includes the unit test coverage, based on the smart contract code, documentation, and requirements presented by the SyntheX team. The coverage is calculated based on the set of Hardhat framework tests and scripts from additional testing strategies. However, to ensure the security of the contract, the Blaize.Security team suggests that the SyntheX team launch a bug bounty program to encourage further active analysis of the smart contracts.
SECURITY ANALYSIS REPORT
Finally, we have provided the SyntheX team with the smart contracts security analysis report. The document contains all the detected risks and possible ways of their mitigation, as well as issues, vulnerabilities, and recommendations for fixes and improvements. Besides, the report contains the confirmation of fixes and necessary explanations from the SyntheX team.
DISCOVER MORE ABOUT THE SECURITY SERVICES AND REQUEST FREE AUDIT ESTIMATION.
AUDIT RESULT
Firstly, the Blaize Security auditors team must mention that protocol has its own Oracle contracts, which utilize Chainlink, Aave, and Compound feeds. Though, Oracle contracts themselves are out of the scope of the current audits. Our team highly recommends utilizing several price sources, having a TWAP-like solution, or using Chainlink or other oracles aggregating several sources. Dependency of the synthetic on a single price source increases the risk of price manipulation through the 3rd party pool manipulation.
The security team performed an extensive manual audit during the testing stage and covered several checklists for common attack vectors and possible exploit possibilities. The team found several critical and high-risk issues with collateral withdrawal, fee calculation during the liquidation, and ETH transfer.
Another noticeable issue was connected to ETH and WETH’s identical support. After the audit, the SyntheX team added WETH support with mandatory ETH wrapping in the protocol, and the security team rechecked fixes with appropriate tests.
The code is well documented with Natspec and internal comments and contains important examples in crucial code places. The overall security is high enough, though the security team decreased the final rating a bit because of the dependency on oracles, which were out of the scope, the centralization aspect because of contract upgradeability, and several issues where the team has taken responsibility at.
From all aspects, SyntheX protocol has passed the security audit and can be evaluated as Highly Secure, 9.6 out of 10.
See the complete list of found vulnerabilities and recommendations about their improvements in this document:
SyntheX_audit_report



