THE SECOND SMART CONTRACT SECURITY AUDIT FOR EVERSTAKE
Everstake is a responsible validator trusted by 625k+ users across 70+ blockchain networks, created by engineers for the entire community in 2018. It’s a self-funded, profitable business employing 125+ people and running over 8,000 nodes.
The Blaize Security team was happy to conduct the second smart contract security audit for Everstake. You can read the first one here.
ABOUT THE PROJECT
The Blaize Security team has conducted an audit of the Everstake B2C protocol. Сheck the repository here.
Everstake is a protocol that allows users to stake their ETH to receive rewards. It uses a list of validators, and each is registered as an Ethereum validator by staking 32 ETH under him. For example, if 100 users have a stake of 32 ETH in total, the protocol sends 32 ETH to the Beacon deposit smart contract to register one validator on the list.
The audit’s goal was to verify the security of staking, withdrawal, and collection of rewards mechanisms and validate the security of users’ funds. Also, audit smart contracts against the list of common vulnerabilities as well as our internal checklist, and check that contracts are optimized in terms of gas usage.
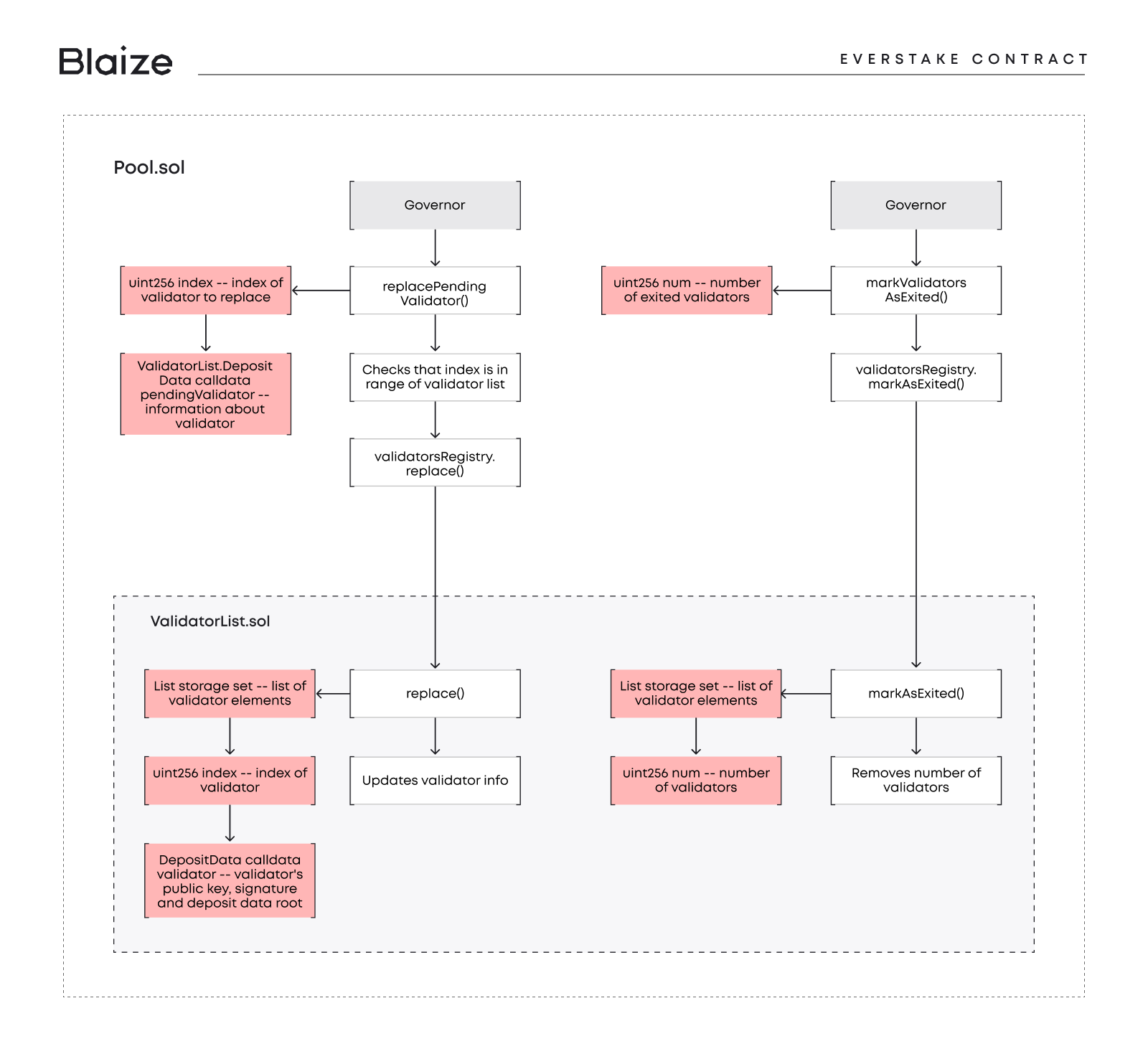
MAIN REQUIREMENTS
We were assigned to detect and describe security issues in the smart contract of Everstake.
We needed to check the smart contracts with the following parameters:
- Whether the contract is secure;
- Whether the contract fully matches requirements from ETH Beacon staking
- Whether the funds flow from the user to the stake contracts is secure and can not be interrupted;
- Whether the contract corresponds to the documentation;
- Whether the contract meets best practices in terms of the efficient use of gas and code readability.
We have scanned this smart contract for commonly known and more specific vulnerabilities:
- Unsafe type inference;
- Timestamp Dependence;
- Reentrancy;
- Implicit visibility level;
- Gas Limit and Loops;
- Transaction-Ordering Dependence;
- Unchecked external call – Unchecked math;
- DoS with Block Gas Limit;
- DoS with (unexpected) Throw;
- Byte array vulnerabilities;
- Malicious libraries;
- Style guide violation;
- ERC20 API violation;
- Uninitialized state/storage/ local variables;
- Compile version not fixed.
In addition, Everstake was checked against less common vulnerabilities from the internal Blaize.Security knowledge base.
SMART CONTRACT SECURITY AUDIT PROCEDURE
Blaize.Security has an established security audit procedure. It includes the following steps:
- Manual code review;
- Static analysis by automated tools;
- Business logic review and decomposition of the system;
- Unit test coverage check;
- Extensive integration testing;
- Fuzzy and exploratory testing;
- Providing a detailed report of detected issues;
- Verification of fixes;
- Final audit report preparation & publishing.
AUTOMATED TOOLS ANALYSIS
The auditors scanned the contract with several publicly available automated analysis tools with the manual verification of all the issues detected with these tools.
MANUAL CODE REVIEW
Scanning contracts by several publicly available automated analysis tools such as Mythril, Solhint, Slither, and Smartdec.
Manual verification of all the issues found with tools.
UNIT TEST COVERAGE
The scope of the audit includes the unit test coverage, which is based on the smart contract code, documentation and requirements presented by the Everstake team. The coverage is calculated based on the set of Hardhat framework tests and scripts from additional testing strategies. However, to ensure the security of the contract, the Blaize.Security team suggests that the Everstake team launch a bug bounty program to encourage further active analysis of the smart contracts.
SECURITY ANALYSIS REPORT
In the end, we have provided the Everstake team with a smart contract security analysis report. The document contains all detected risks and the possible variants of their mitigations, issues, vulnerabilities details, and recommendations for their improvements.
FIND OUT MORE ABOUT THE SECURITY SERVICES AND REQUEST FREE AUDIT ESTIMATION.
AUDIT RESULT
During the audit, a critical issue was identified regarding access control. Thus, it was pointed out that anyone could set the super admin account while the super admin was equal to zero address.
In this case, a malicious actor could have been monitoring the mempool to search for deployment or setting super admin to zero address and using a front-run attack to set his address. The Everstake team has successfully fixed the issue.
The other issues were connected to iteration through the whole storage array, lack of events, and several gas optimizations. All of them were successfully fixed as well.
The overall security of smart contracts is high enough: they have passed all the security checks and the overall security of the smart-contracts system of Everstake protocol can be evaluated as Highly Secure, 9.8 out of 10.
See the complete list of found vulnerabilities and recommendations about their improvements in this document:
Everstake_audit_report



